Threat Intelligence Guides
Random and interesting URLScan queries. Use these as an educational resource, or as starting points for investigations and experimentation.
Lumma Stealer
- domain, alphabetical characters
- any top level domain (TLD)
- file url ends in
/api - Hosted on CloudFlare
page.url:/https?:\/\/[a-z]+\.[a-z]+\/api/ AND page.server:cloudflare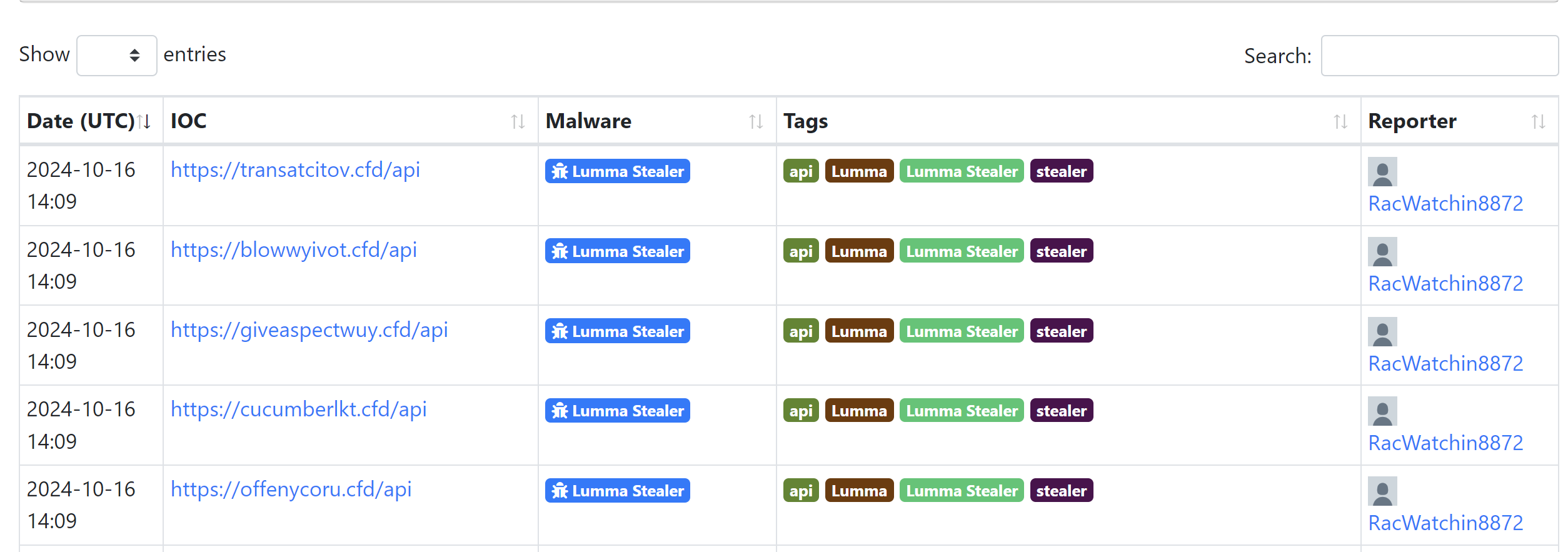
Stealc
- ip address
- 16 character
.phpfile, containing letters and numbers
page.url:/https?:\/\/[0-9\.]+\/[a-z0-9]{16}\.php/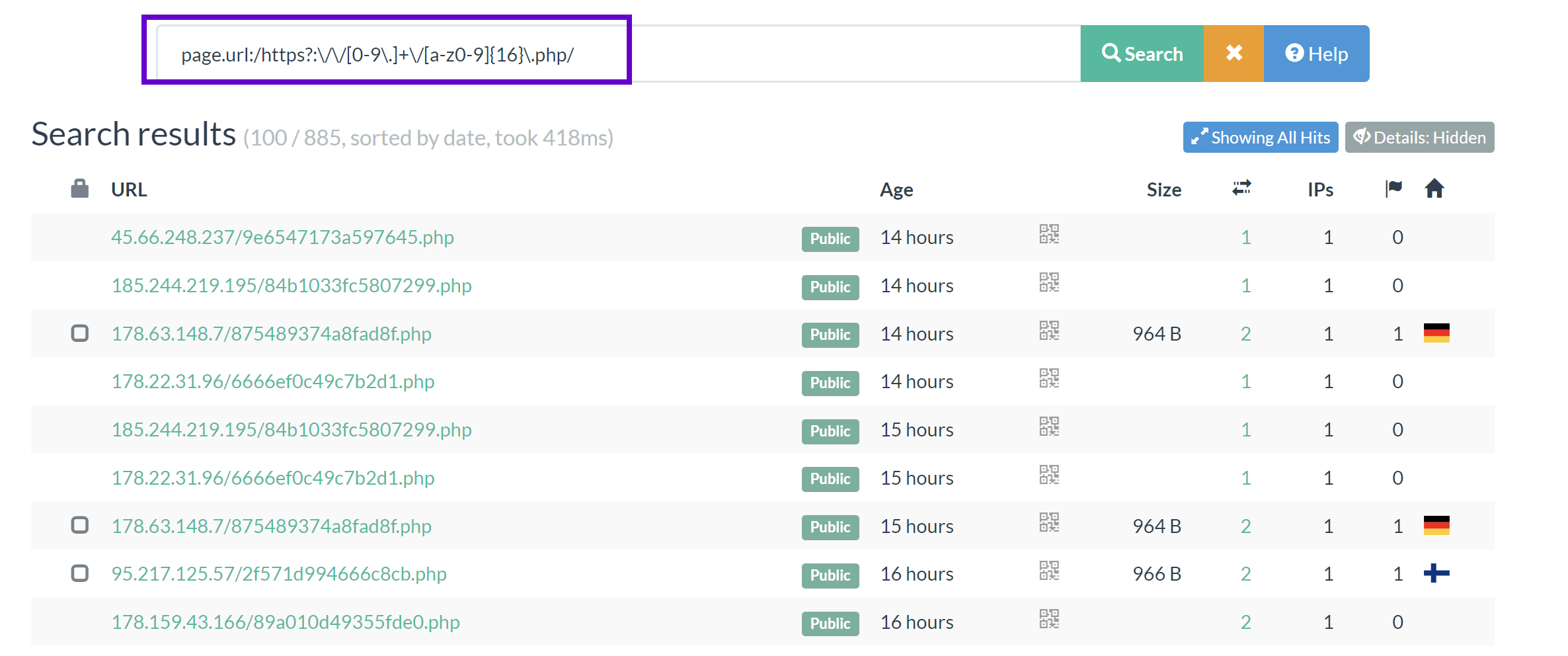
MassLogger/VIPKeylogger
- IP Address, no domain
/txt/folder- 13-18 character
.exefile
page.url:/https?:\/\/[0-9\.]+\/txt\/[a-z0-9]{13,18}\.exe/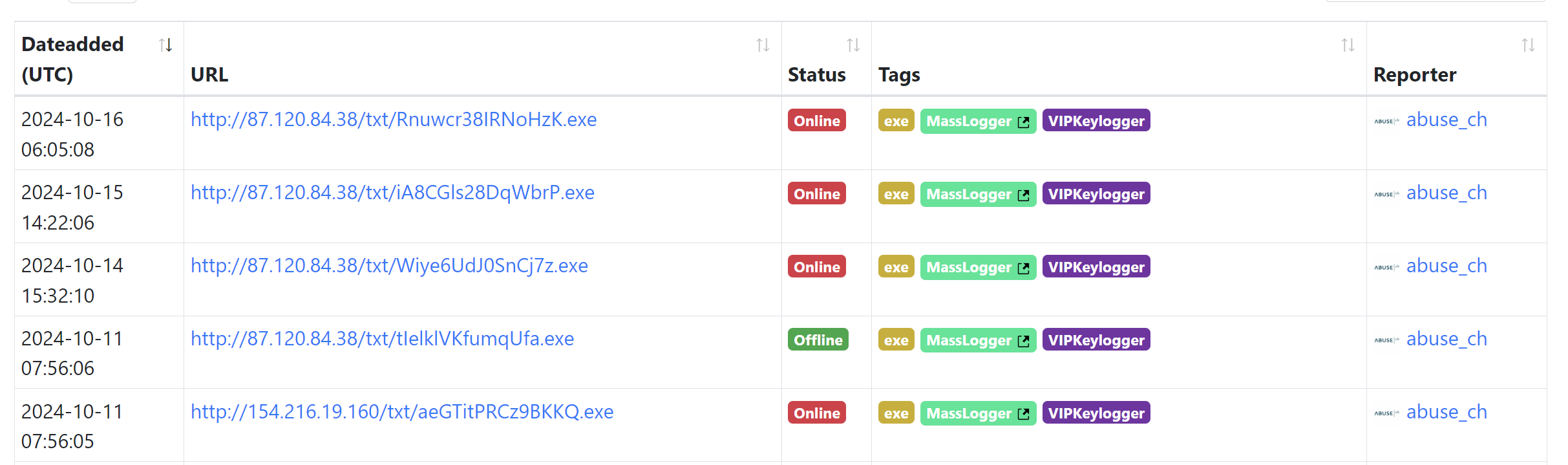
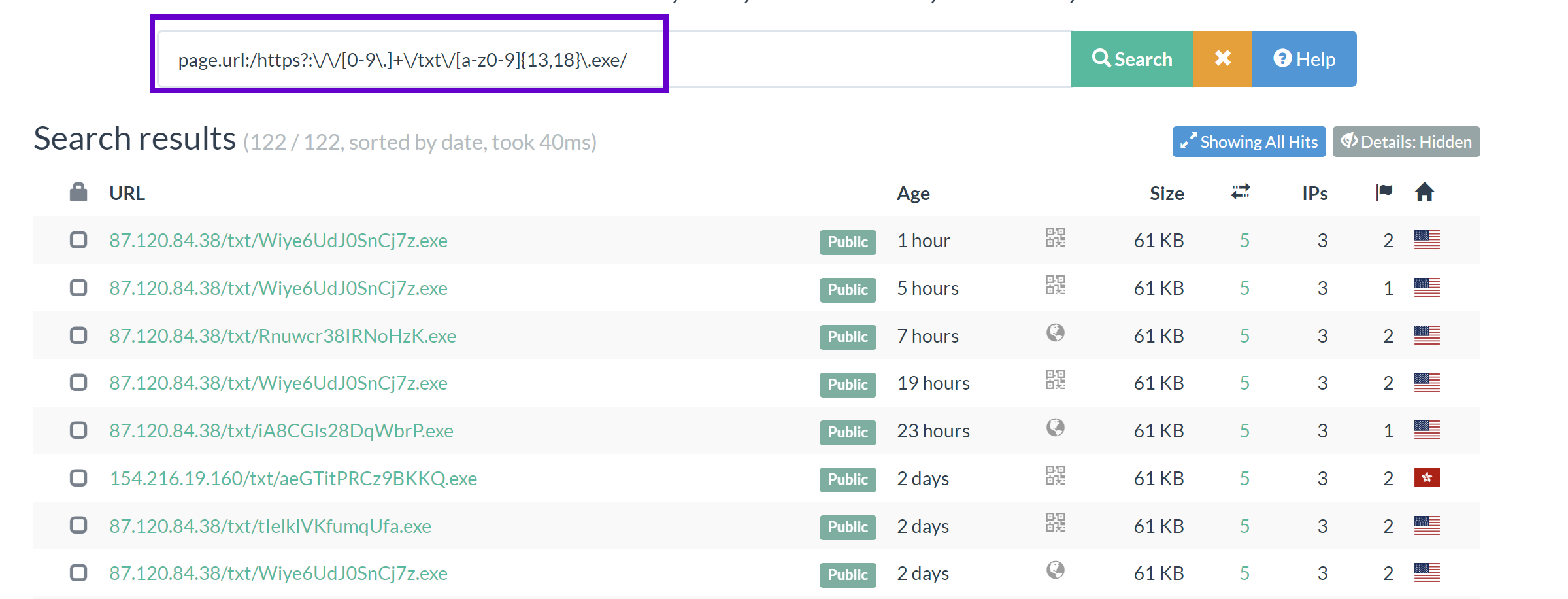
FakeUpdates
- domain name, alphabetical characters
- Any top level domain
- folder name of
font - Any
.phpfile as filename
page.url:/https?:\/\/[0-9a-z]+\.[a-z]+\/font\/[a-z]+\.(php)/ AND page.mimeType:"text/html" AND stats.requests:2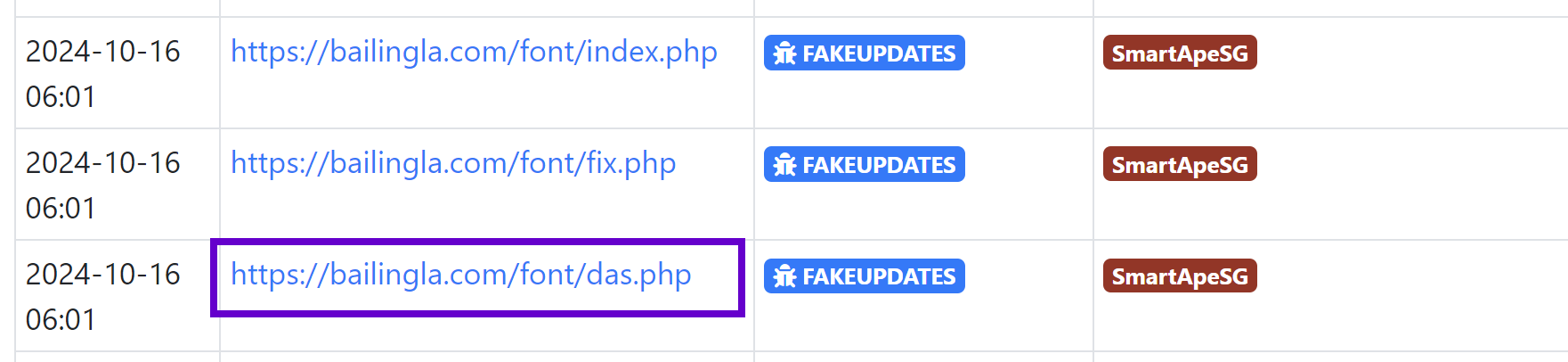
MassLogger?
- ip address (no domain)
- htdocs as folder name
- .exe file, approx 15 characters long (allowing for 13-18)
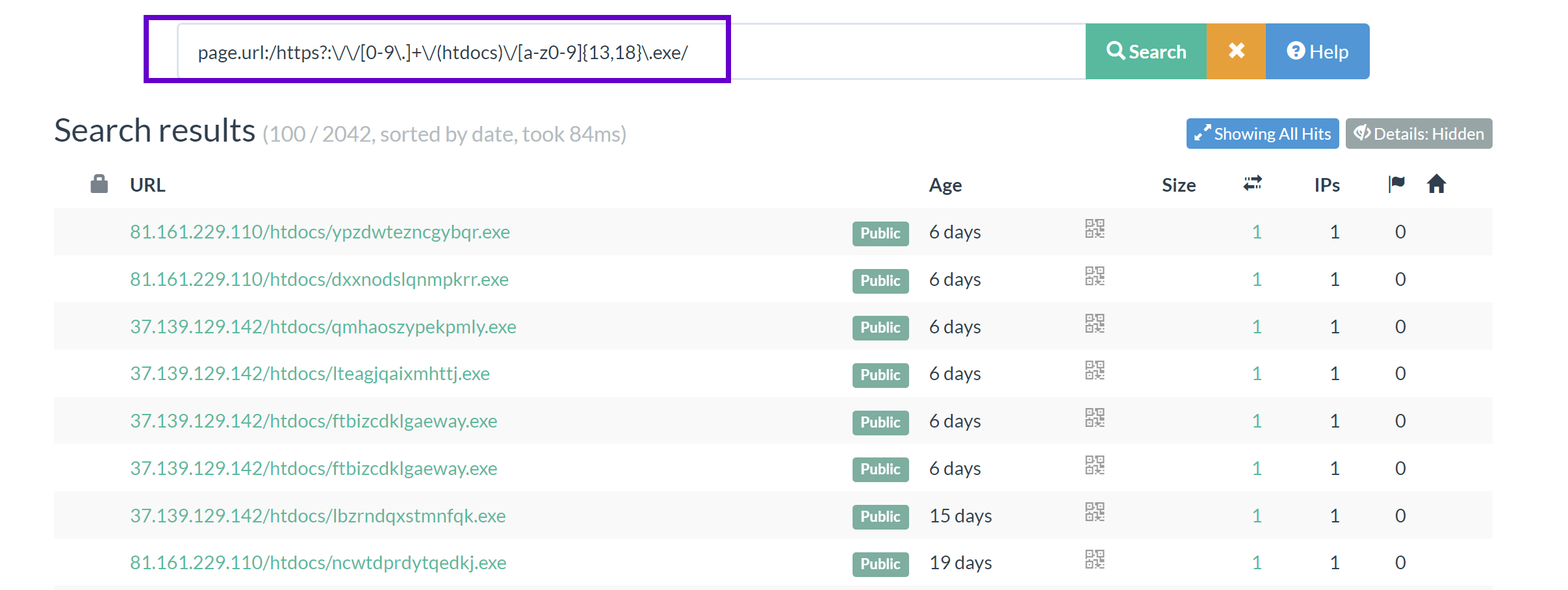
page.url:/https?:\/\/[0-9\.]+\/(htdocs)\/[a-z0-9]{13,18}\.exe/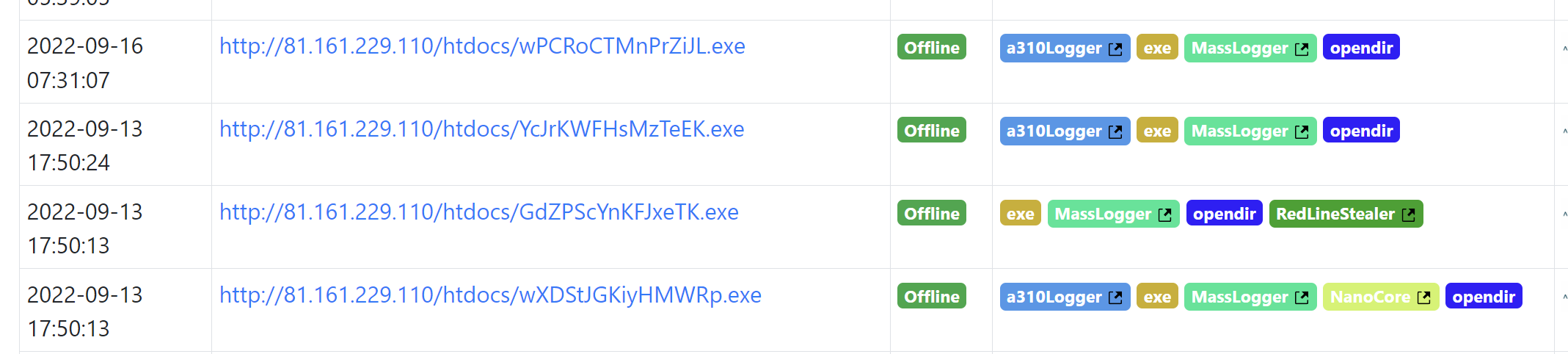
StealC Again
- http or https
- IP (no domain name)
- 16 character folder name
- FileName of
sqlite3.dll, mozglue.dll, or vcruntime140.dll
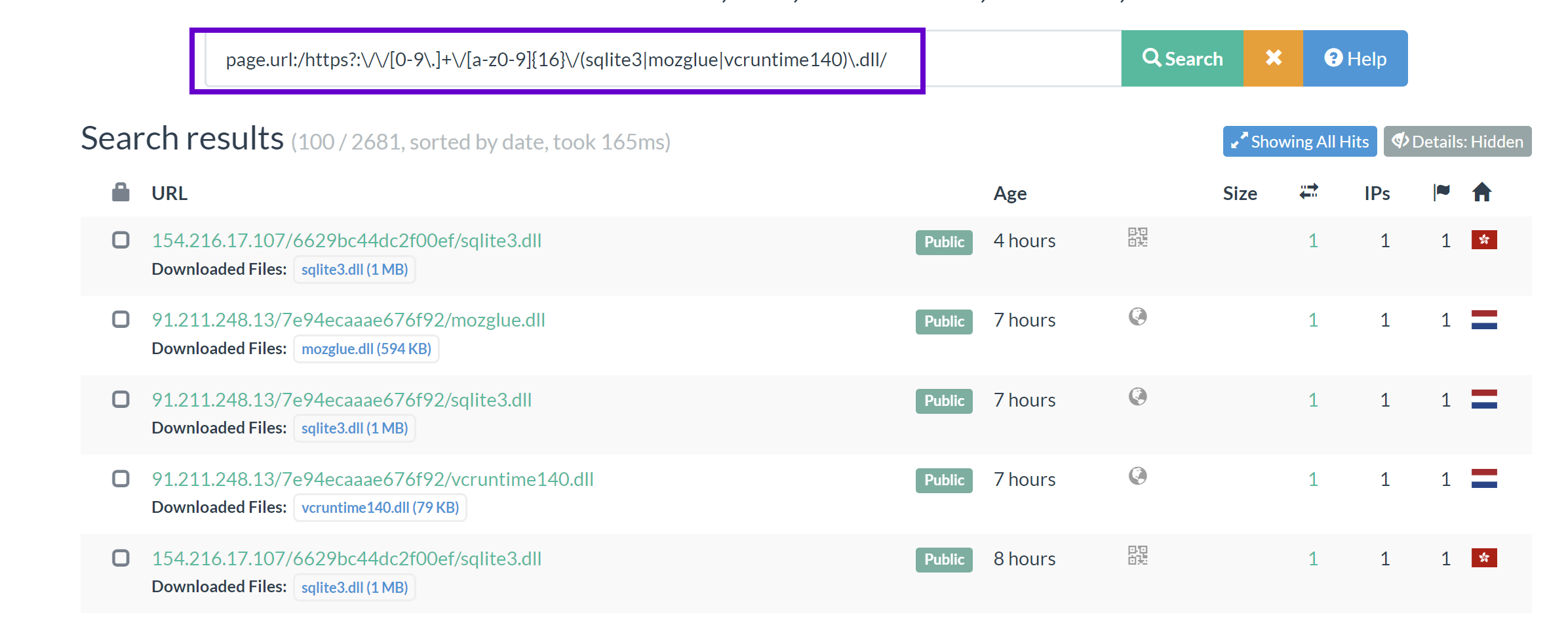
page.url:/https?:\/\/[0-9\.]+\/[a-z0-9]{16}\/(sqlite3|mozglue|vcruntime140)\.dll/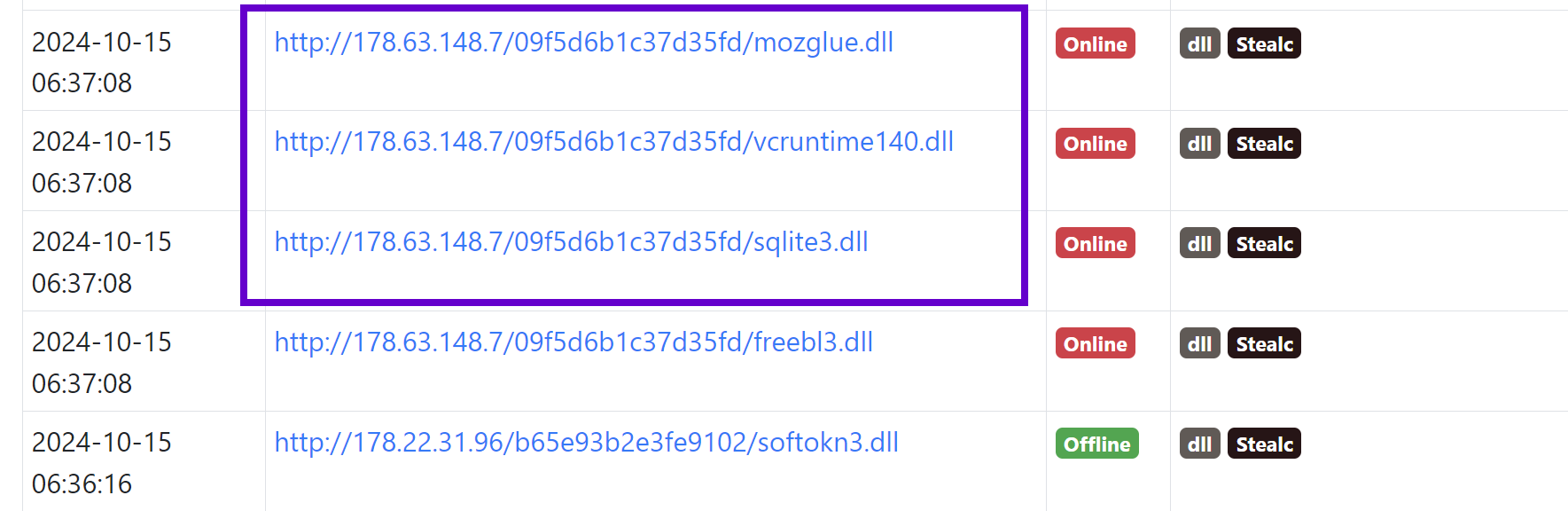
DCRAT
- 8 character subdomain, 1 letter, 7 numbers
- Any primary domain, alphabetical characters
- Any top level domain
- 8 character
.phpfile
page.url:/https?:\/\/[a-z][0-9]{7}\.[a-z]+\.[a-z]+\/[a-z0-9]{8}\.php/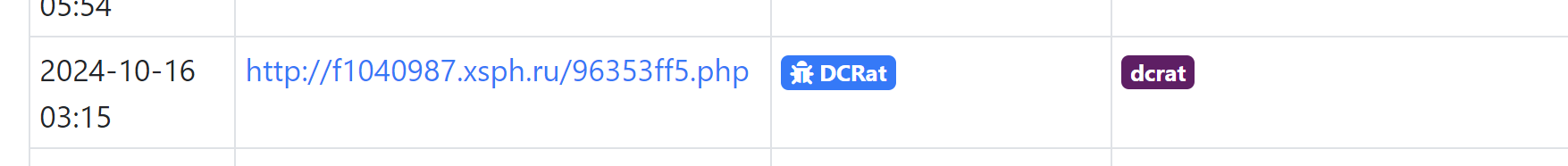
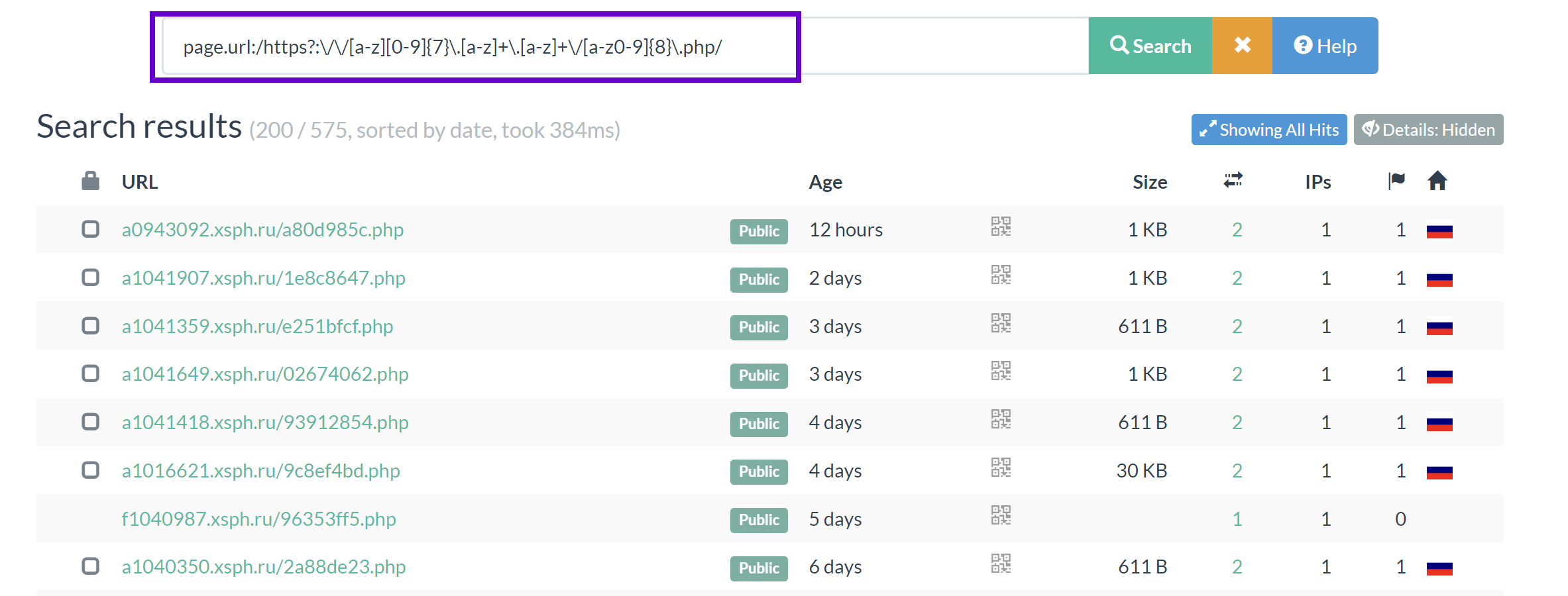
Amadey
- IP Address
- 8-10 character folder name, mostly random
- URL ending in
/index.php - 404 error
page.url:/https?:\/\/[0-9\.]+\/[a-z0-9]{8,10}\/index.php/ AND page.status:404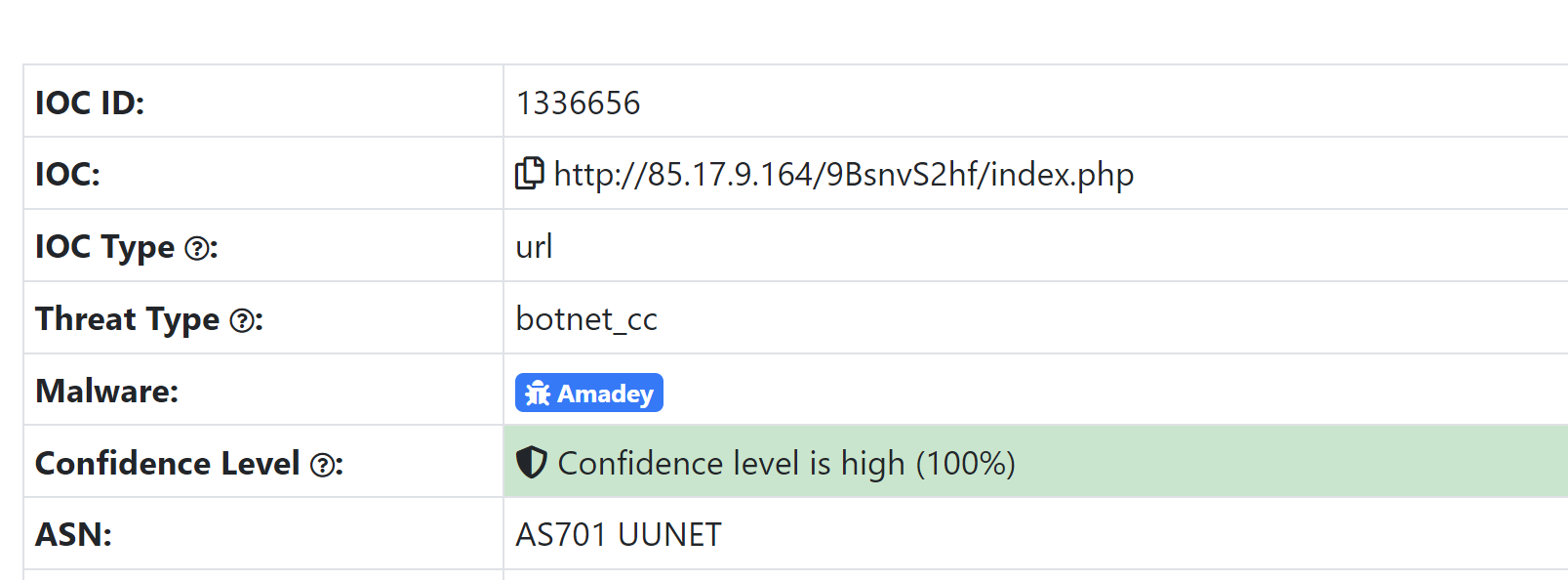
SmartLoader
- IP Address
/task/folder- 40 character filename with no extension
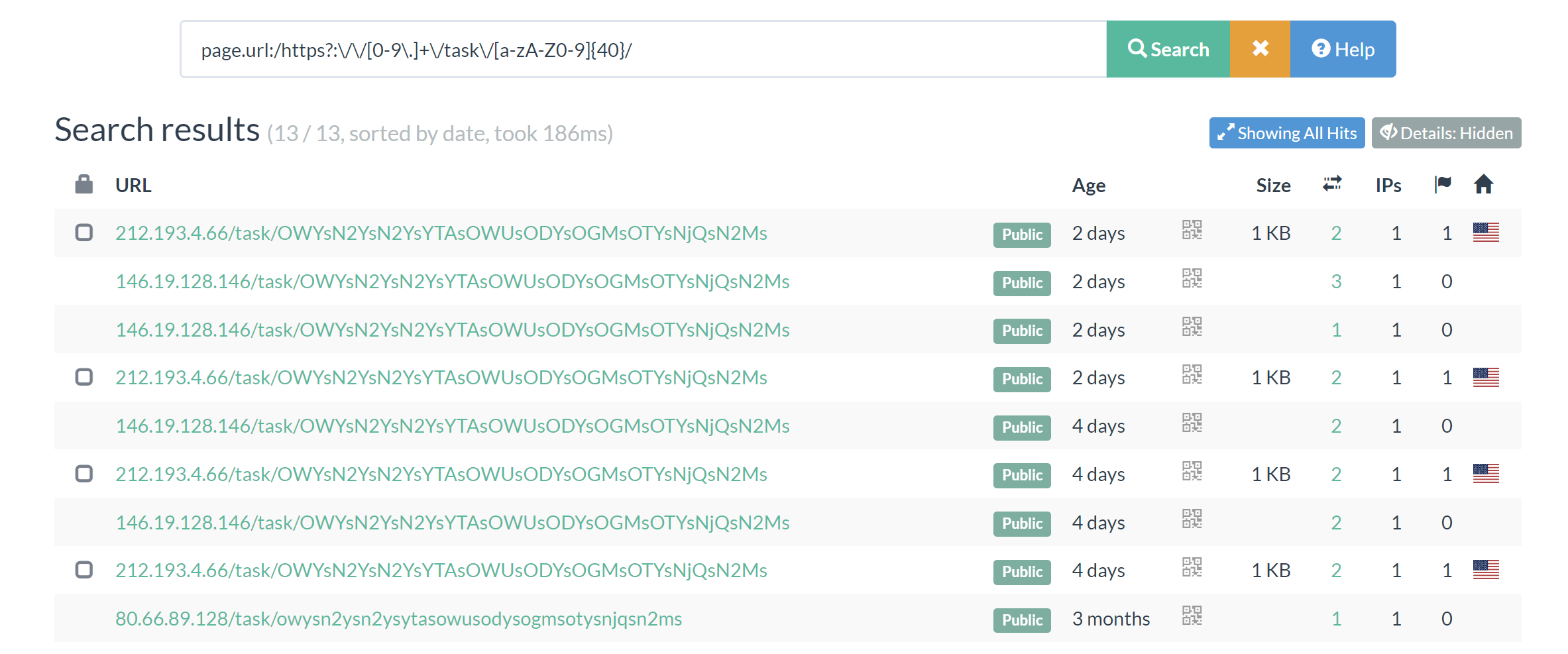
page.url:/https?:\/\/[0-9\.]+\/task\/[a-zA-Z0-9]{40}/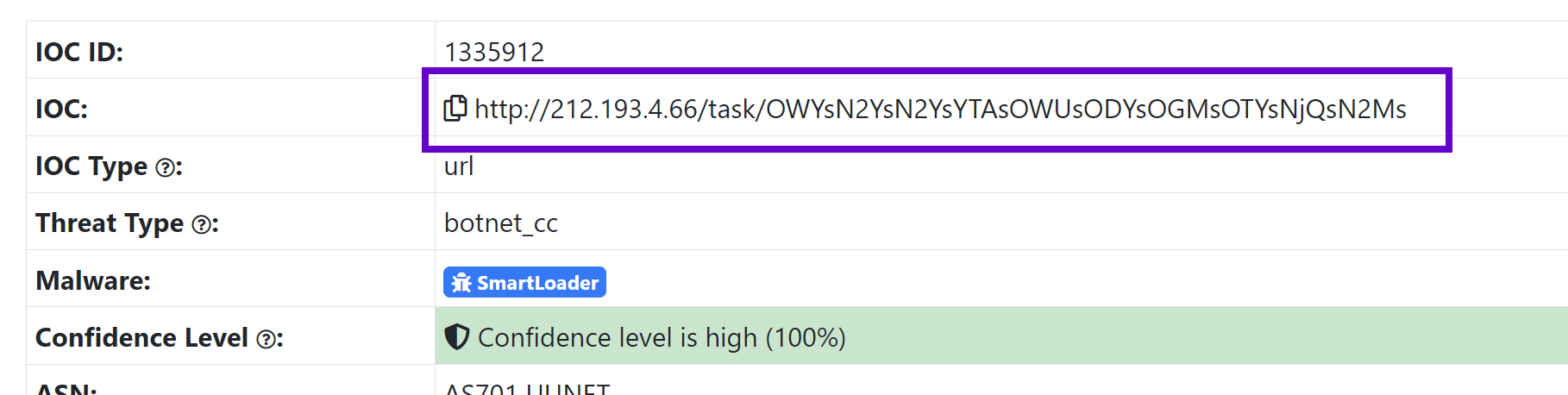
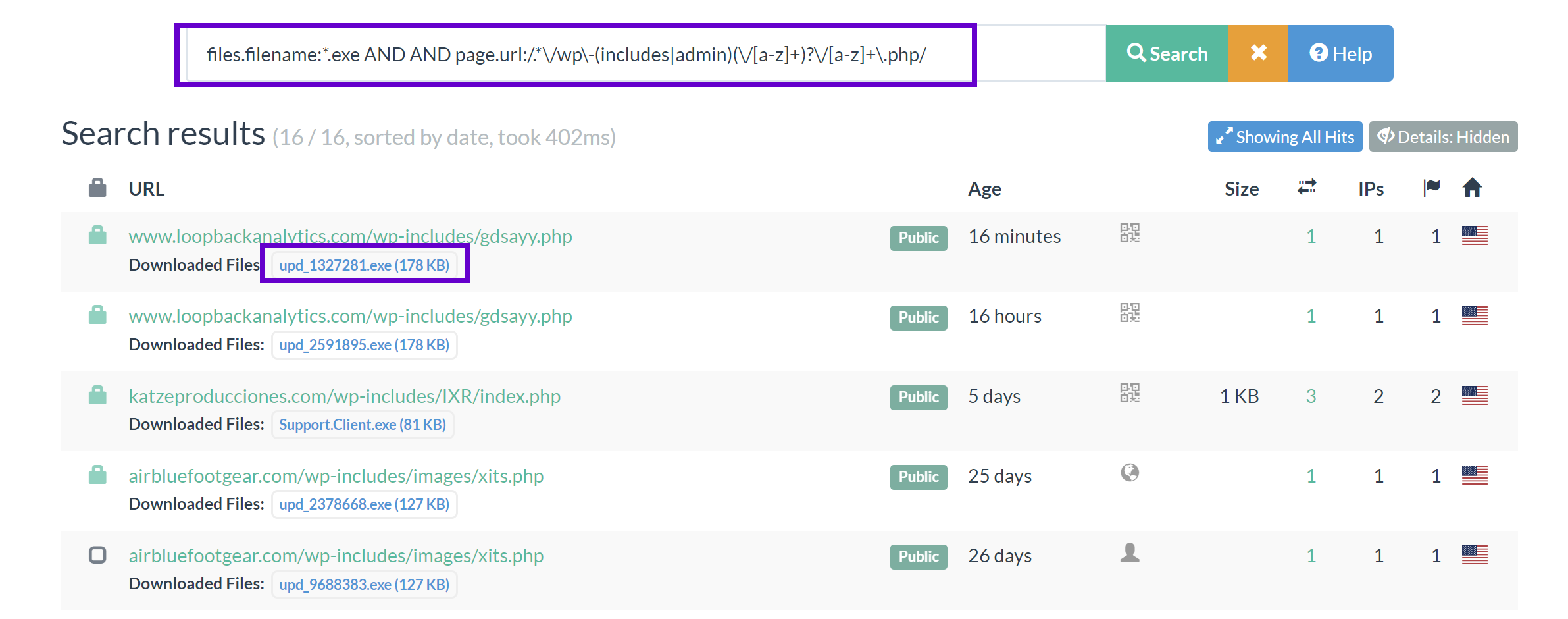
Executable Files From WordPress Sites
- Any Domain or IP
wp-adminorwp-includesfolder- URL ending in
.phpfile - Saved File is an
.exe
files.filename:*.exe AND AND page.url:/.*\/wp\-(includes|admin)(\/[a-z]+)?\/[a-z]+\.php/