Practical Examples Of Malware Infrastructure Discovery With Passive DNS
Practical Examples Of Malware Infrastructure Discovery With Passive DNS | Validin
Exploring five practical examples that any analyst can use to uncover malicious infrastuructre with Passive DNS

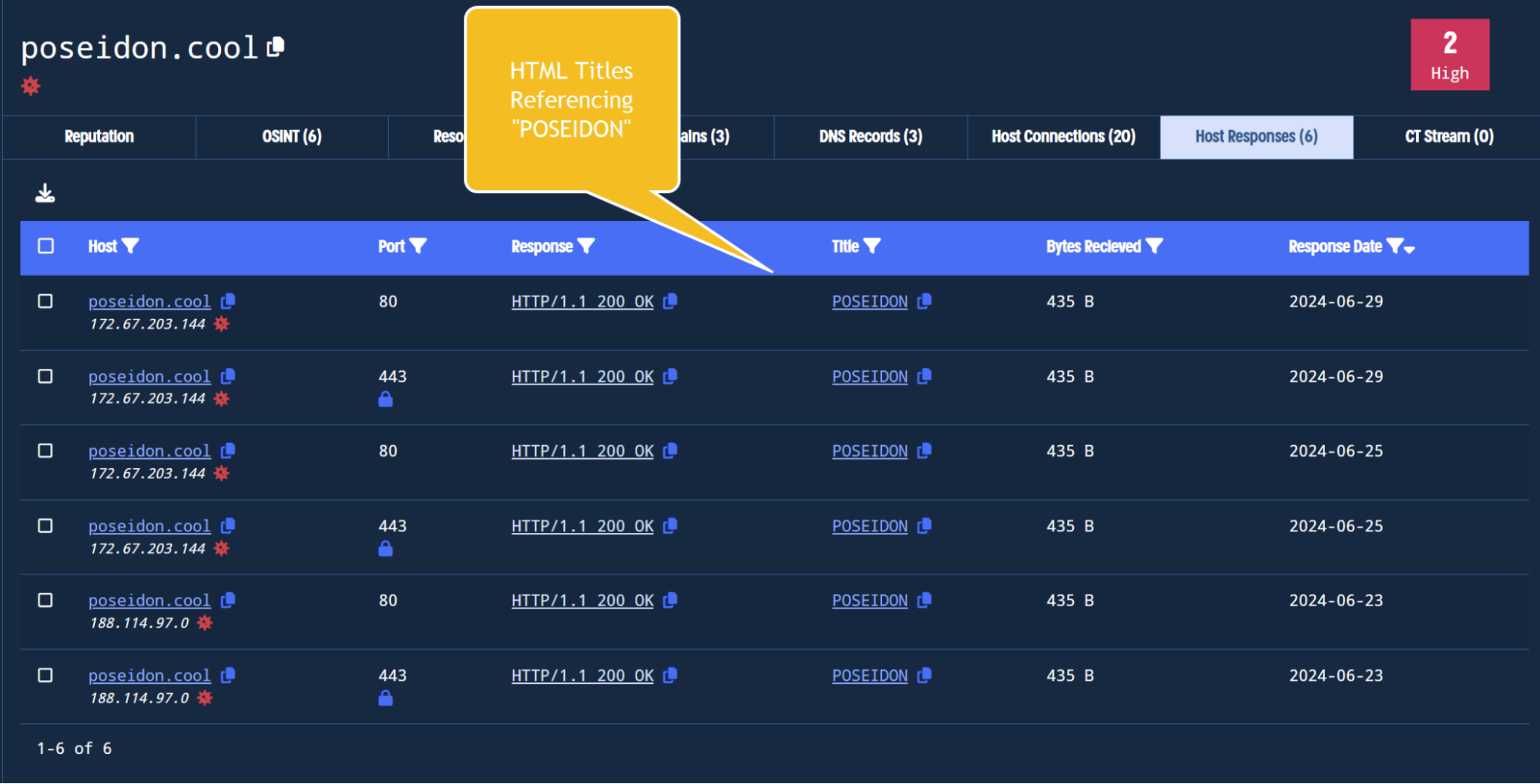
Poseidon Analysis - Quick and Intuitive Workflows with Validin
Poseidon Analysis - Quick and Intuitive Workflows with Validin | Validin
How to quickly and easily identify threat infrastructure through DNS history and pivoting
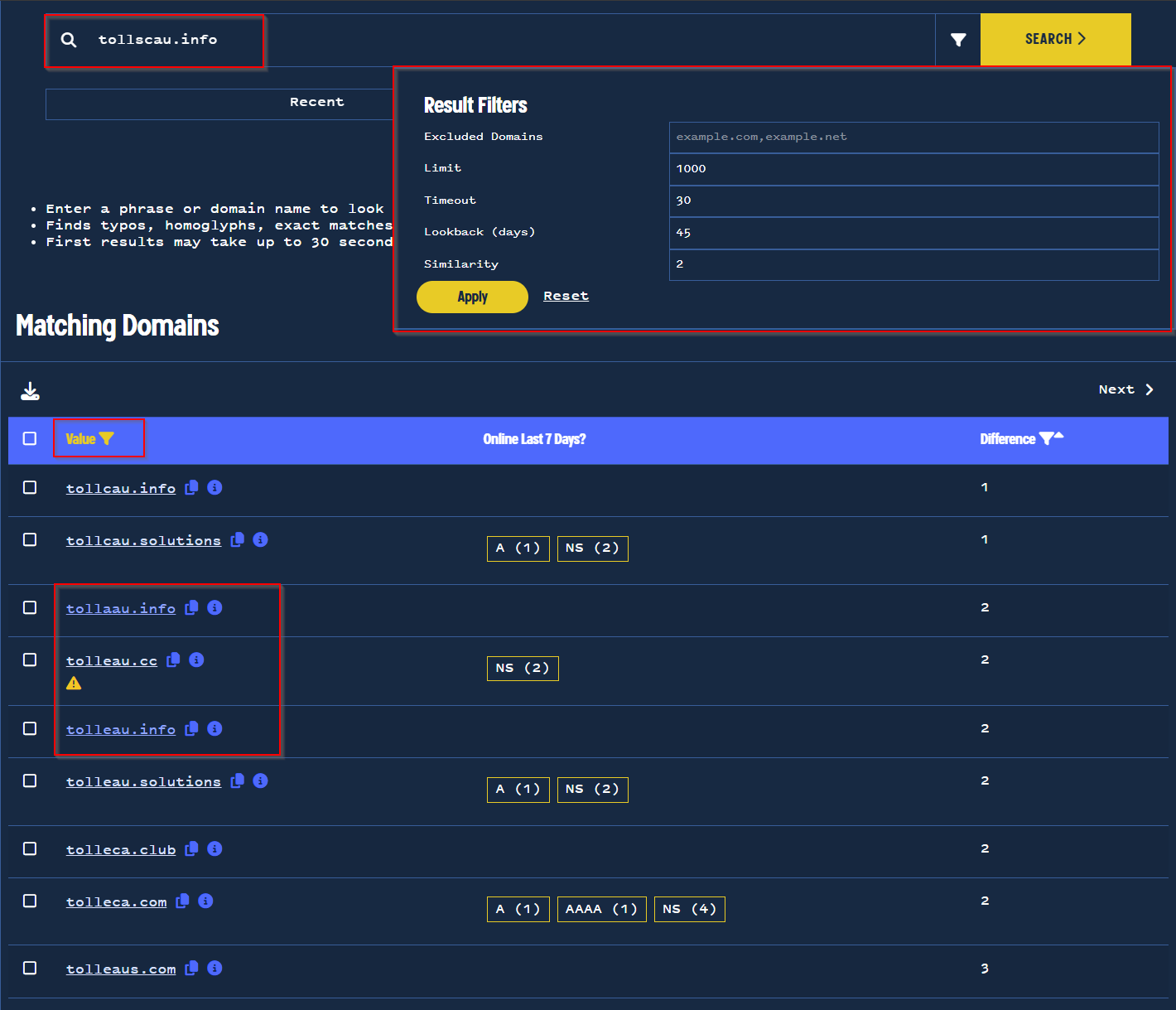
Revealing Australian Toll Spammer Infrastructure With PDNS
Revealing Australian Toll Spammer Infrastructure With PDNS | Validin
Leverage passive DNS analysis to identify malicious domains behind spam campaigns targeting Australians. Fortify your organization’s spam defenses with Validin.
A Beginner’s Guide to Tracking Malware Infrastructure
A Beginner’s Guide to Tracking Malware Infrastructure
Find approachable and high-value methods that can be used to hunt for malware infrastructure in this guest blog from Embee Research.
A Beginner’s Guide to Hunting Malicious Open Directories
A Beginner’s Guide to Hunting Malicious Open Directories
In this guest blog, Embee Research covers the basics of a malicious open directory, how you can discover them during threat hunting.

Hackers No Hashing: Randomizing API Hashes to Evade Cobalt Strike Shellcode Detection
Hackers No Hashing: Randomizing API Hashes to Evade Cobalt Strike Shellcode Detection | Huntress
Hackers could be outsmarting preventive tools by making trivial changes to default settings. We dive into our research in this blog.

Snakes on a Domain: An Analysis of a Python Malware Loader
Snakes on a Domain: An Analysis of a Python Malware Loader | Huntress
Join us on a threat analysis journey as we discover a very shady Python—and a very friendly RAT.

Cobalt Strikes Again: An Analysis of Obfuscated Malware
Cobalt Strikes Again: An Analysis of Obfuscated Malware | Huntress
Join us for a threat hunting adventure as we analyze a suspicious run key that leads us to Cobalt Strike malware hidden across nearly 700 registry values.



